The Institute of Internal Auditors defines internal auditing in this way:
"Internal auditing is an independent, objective assurance and consulting activity designed to add value and improve an organization's operations. It helps an organization accomplish its objectives by bringing a systematic, disciplined approach to evaluate and improve the effectiveness of risk management, control, and governance processes."
The following items are a sampling of the things we do:
- Evaluate your operations for ways to improve your effectiveness or efficiency.
- Help you comply with various university, State and Federal policies.
- Ensure that you have proper controls in place to protect you, your employees and the University.
- Provide you with advice regarding systems, policies, procedures, etc.
The Institute of Internal Auditors defines internal controls as any action taken by management, the board, and other parties to manage risk and increase the likelihood that established objectives and goals will be achieved. Internal Controls are the methods or procedures used by an organization to:
- ensure reliability and integrity of information
- ensure compliance with policies, laws, regulations, procedures, contracts
- safeguard assets
- promote economical and efficient use of resources
- accomplish goals and objectives
Generally, there are two types of controls: preventive and detective. Both types of controls are essential to an effective internal control system. From a quality standpoint, preventive controls are essential because they are proactive and emphasize quality. However, detective controls play a critical role by providing evidence that the preventive controls are functioning as intended.
Preventive Controls are designed to discourage errors or irregularities from occurring. They are proactive controls that help to ensure departmental objectives are being met. Examples of preventive controls are:
- Segregation of Duties: Duties are segregated among different people to reduce the risk of error or inappropriate action. Normally, responsibilities for authorizing transactions, recording transactions and handling the related asset are divided. (Example: the individual collecting cash and depositing funds should be someone different than the individual responsible for entering that data into the system.)
- Approvals, Authorizations, and Verifications: Management authorizes employees to perform certain activities and to execute certain transactions within limited parameters. In addition, management specifies those activities or transactions that need supervisory approval before they are performed or executed by employees. A supervisor’s approval implies that he or she has verified and validated that the activity or transaction conforms to established policies and procedures. (Example: Processing vouchers only after signatures have been obtained from appropriate personnel.)
- Security of Assets (Preventive and Detective): Access to equipment, inventories, securities, cash and other assets is restricted; assets are periodically counted and compared to amounts shown on control records. (Example: door locks and alarm system; physical inventory of equipment is counted and compared to records in Sunflower, the university's fixed asset system.)
Detective Controls are designed to find errors or irregularities after they have occurred. Examples of detective controls are:
- Reviews of Performance: Management compares information about current performance to budgets, forecasts, prior periods, or other benchmarks to measure the extent to which goals and objectives are being achieved and to identify unexpected results or unusual conditions that require follow-up. (Example: comparing forecasted athletic ticket sales to the actual results and investigating significant variances.)
- Reconciliations: An employee relates different sets of data to one another, identifies and investigates differences, and takes corrective action, when necessary. (Example: Reconciling FIS Monthly Detail Reports to departmental records.)
Who is responsible for internal controls?
Everyone plays a part in James Madison University's internal control system. Ultimately management is responsible for ensuring that controls are in place. That responsibility is delegated to each area of operation. Every employee has some responsibility for making this internal control system function. Therefore, all JMU employees need to be aware of the concept and purpose of internal controls. Audit and Management Services is here to help you achieve that goal.
Framework for Internal Controls Evaluation
University Policy 1108 (Internal Controls) assigns primary responsibility for maintaining adequate internal controls to academic and administrative department heads, with vice presidents having ultimate responsibility for their divisions.
We use the COSO (Committee of Sponsoring Organizations of the Treadway Commission) Integrated Framework (2013) to evaluate internal controls over university business activities. COSO provides three categories of objectives which allow organizations to focus on differing aspects of internal control:
Operations Objectives pertain to effectiveness and efficiency of the entity’s operations, including operational and financial performance goals, and safeguarding assets against loss.
Reporting Objectives pertain to internal and external financial and non-financial reporting and may encompass reliability, timeliness, transparency, or other terms as set forth by regulators, recognized standard setters or the entity’s policies.
Compliance Objectives pertain to adherence to laws and regulations to which the entity is subject.
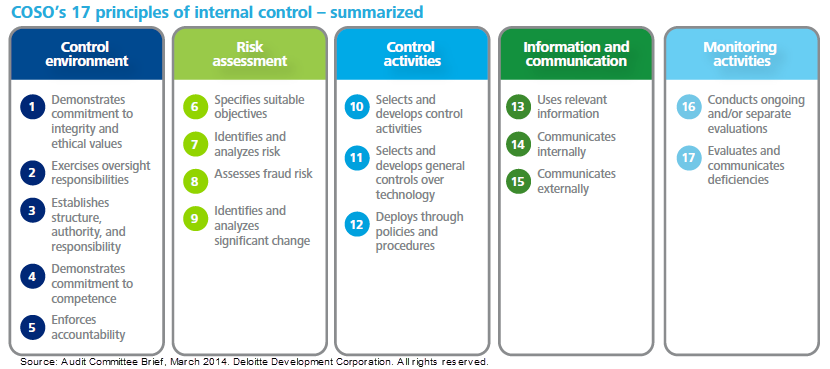
Principles 1 and 2 are assessed via reviews of governance, risk assessments and enterprise risk management projects. Principles 3 through 9 and 13 through 17 are reviewed during preliminary work on the audit. Operational audits typically focus on principles 10, 11 and 12 as they are most directly related to controlling business processes.
Audit and Management Services has gathered sufficient and relevant information to support an opinion for the identified activities. Our opinion may be that the internal controls are:
- effective
- partially effective
- not effective
“Internal controls are effective” means that:
- Each of the five internal control components and relevant principles are present and functioning.
- The five components are operating together in an integrated manner.
How does my department rate?
Now that you've had a brief introduction to internal controls, you may use the Internal Controls Self-Assessment to evaluate controls for specific functions.
The Institute of Internal Auditors defines risk as "The possibility of an event occurring that will have an impact on the achievement of objectives. Risk is measured in terms of impact and likelihood. Examples of adverse events, which may occur due to the absence of internal controls or the ineffective use of resources, include:
- noncompliance with Federal and State laws
- cash receipts lost or stolen
- incorrect payroll amount to be paid to employee
- inaccurate or incomplete data
- inadequately trained staff
- any form of embarassment
As the University increases the use of technology, additional risks may exist. Examples of such risks include:
- data breach/leak of protected information
- unauthorized access to student records
- unavailability of critical computer systems
- inappropriate destruction or retention of data
- failure to comply with PCI Data Security Standards
The above actions could be perpetrated by someone within the JMU community or an outsider, therefore increasing the University's vulnerability.
Audit and Management Services performs an annual risk assessment to ensure that key audit areas (departments or activities) at the University are examined on a sufficiently frequent basis. Risk assessment scores for potential audit areas are updated at the conclusion of audits or when we become aware of significant changes (e.g., restructuring, new departments or services, etc.). Also, we request that departments complete a risk survey every other year to ensure that we are aware of major changes. The risk scores for each audit area are derived by assigning numerical ratings for nine weighted risk factors.
The updated risk assessment score is then used to develop the Long Range Audit Plan and Resource Analysis, which covers a five-year period. The frequency of audits for an area is determined by evaluating the level of risk in audit areas. The higher the risk score assigned to a given area, the greater the audit frequency. In addition to scheduled audit areas, the plan also includes time for special projects. Such projects may be requested by University management or may be performed as a result of suspected fraud, waste or abuse.
Annual Audit Plans are derived from the Long Range Plan and, more importantly, input from Vice Presidents. Each year we ask the Vice Presidents to review the Long Range Plan and provide this input. When possible, the Annual Audit Plan is adjusted to incorporate additions or changes suggested by the Vice Presidents. A key goal of our department is to provide adequate resources to address requests from management to do projects involving consultative services, analyses and efficiency reviews.
The Long Range and Annual Audit Plans are approved by the Audit Committee of the Board of Visitors. All audits scheduled for any particular year on the Long Range Plan may not be included on the Annual Audit Plan for that year due to resource constraints, a larger volume of special projects or other variables.
-
Schedule the Audit
Audits are scheduled based upon the annual audit plan approved by the audit committee of the JMU Board of Visitors with input provided by the Audit Committee, Vice Presidents and the President. AMS periodically completes risk assessments for the purposes of audit planning. Risk factors included in the assessment may include financial, compliance, reputational, physical security, health and safety, and other factors. Audits with higher risks are given priority over lower risk audits. -
Request Information
The Vice President, Assistant Vice President or Dean, and the Department Head are notified that an audit will be performed. Specific information required to begin the audit is requested at this time. -
Determine the Scope of an Audit
After reviewing the information provided by the department and further discussions with key personnel, the scope of the audit is determined and communicated to the Vice President, Assistant Vice President and Department Head. -
Develop Understanding of Activities
A detailed understanding of each activity included in the scope of the audit is developed by reviewing policies and procedures, examining documentation provided by the department and interviewing key personnel. The department and AMS then identify the risks and controls associated with these activities. -
Evaluate Internal Controls
AMS evaluates the design and application of internal controls identified for each activity included in the scope of the audit. Standard controls (e.g., authorizations, approvals, reconciliations, documentation, and segregation of duties) are evaluated as part of this process. If control weaknesses are found, AMS makes recommendations to enhance or establish controls. -
Test Controls: After identifying the controls that are in place for each activity and evaluating controls design and application, AMS develops an audit program to test if the controls are functioning as intended. Compliance with applicable policies or laws is also tested. Errors or exceptions found during testing are discussed with applicable personnel and recommendations to mitigate the risk(s) identified are explored.
-
Draft Audit Report: At the conclusion of the test work, AMS issues a draft report on the effectiveness of controls, including recommendations for improvements. The draft report is sent to the Department Head to provide an opportunity to express concerns or disagreement with the findings and recommendations. A revised draft is issued based on discussions with the Department Head and forwarded to the Assistant Vice President or Dean for review.
-
Exit Conference: A meeting may be scheduled with the Vice President, the Assistant Vice President or Dean, and Department Head to discuss the report. The purpose of this discussion is to provide the department with an opportunity to express concerns or disagreements with the draft opinion and/or recommendations. AMS revises the draft report based on the results of this discussion as necessary.
-
Request Management Responses: After the meeting, the Department Head is asked to provide witten responses to the draft report. AMS incorporates the department's responses into the revised draft and forwards it to the Assistant Vice President or Dean and Vice President for review.
-
Issue Final Report: The final report, which includes management responses, is distributed to the President, Vice President, Assistant Vice President or Dean, and the Department Head. The final report is also distributed to the Audit Committee of the Board of Visitors.
According to University Policy 1603 employees are required to immediately notify the Director of Audit and Management Services of circumstances which suggest that a fraudulent transaction has occurred. Fraudulent transactions can include, but are not limited to, the following prohibited acts:
- misappropriation of cash or funds with falsification of documents
- unauthorized use of University property and resources
- falsifying entries to payroll and travel records
- charging personal purchases to the University
- unauthorized use of University employees/time
Upon notification of a possible fraud, the Director of Audit and Management Services will inform the appropriate Vice President and the President. Audit and Management Services will then complete a review to determine if there is a reasonable possibility that a fraud has occurred. If we conclude that a reasonable possibility of fraud exists, we will prepare a letter for the President's signature reporting the possible fraudulent transaction to the Auditor of Public Accounts and the Department of State Police in accordance with Chapter 14 Section § 30-138 of the State Code of Virginia.
We may also consult with JMU Public Safety. Further investigation of the possible fraud, with the objective of prosecution, is the responsibility of Public Safety, and the appropriate Commonwealth attorney.
In addition, any JMU employee may anonymously report suspicious activities to the State Employee Fraud, Waste and Abuse Hotline (1-800-723-1615 - no caller ID but does accept voicemail), maintained by the Office of the State Inspector General (OSIG). Audit and Management Services may be required to investigate these activities and report findings to OSIG.
